Cyber Attacks in Healthcare: Escalation and Countermeasures
Analysis of the escalation of cyber attacks in the Italian healthcare sector, with high-profile cases, common attack vectors, and practical solutions to strengthen cybersecurity.
Table of Contents
In this article, we will examine the evolution and increasing frequency of hacker attacks on Italian healthcare institutions, reporting some high-profile cases before analyzing the most common attack methods and proposing practical solutions to strengthen cybersecurity in healthcare organizations.
An Increasingly Targeted Sector
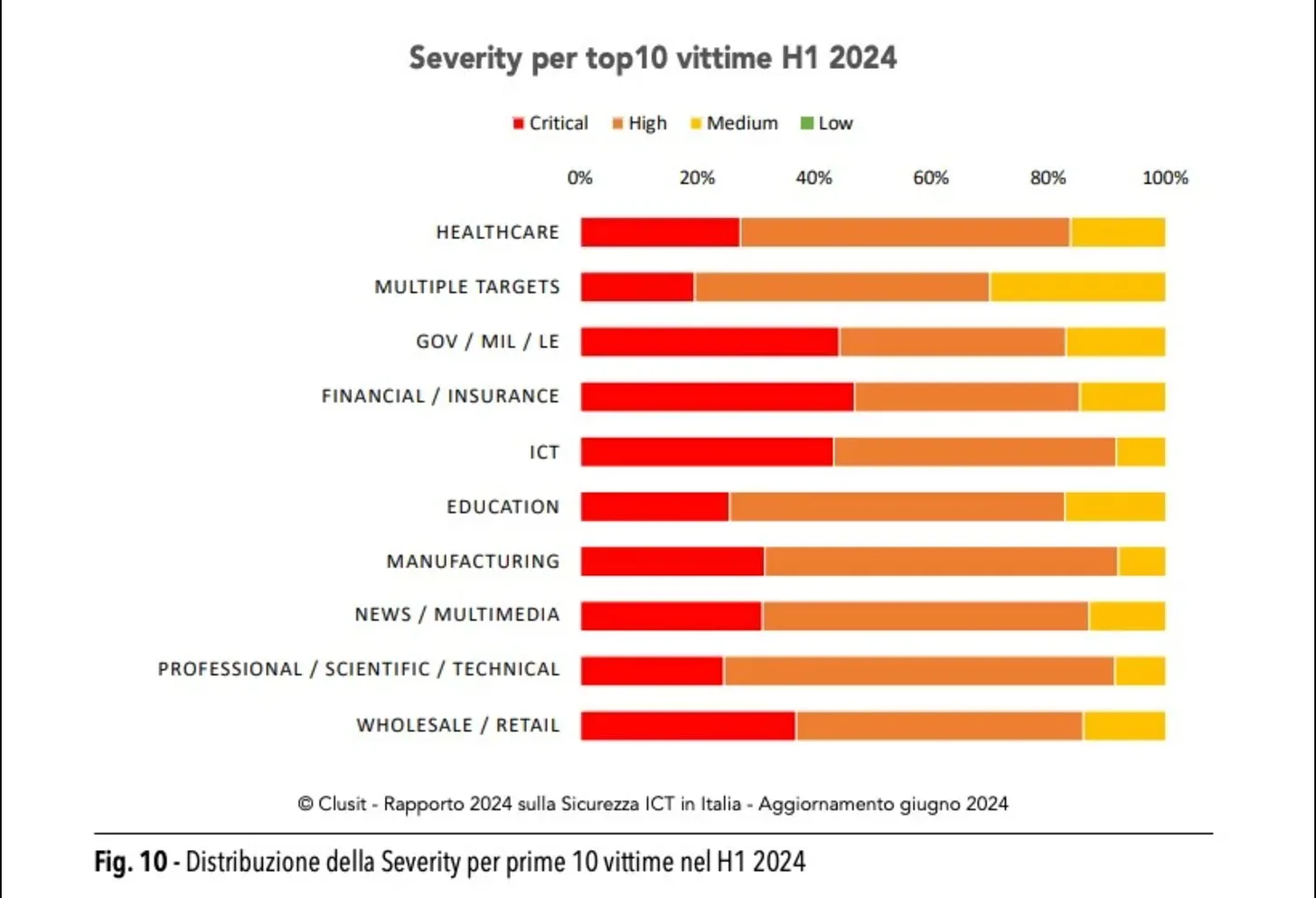
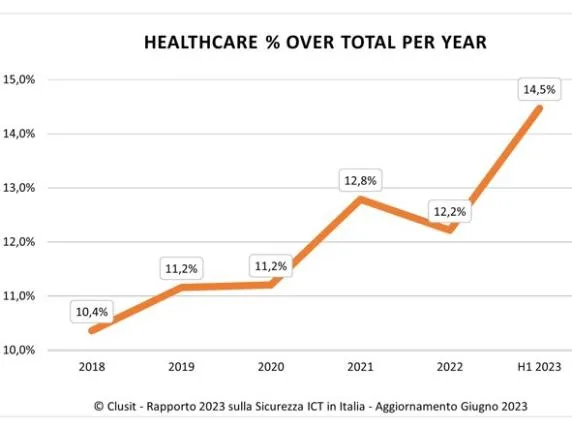
The healthcare sector has become one of the primary targets for cybercriminals worldwide. The data confirms this: according to the Clusit 2024 Report, healthcare is actually the most attacked sector in the world (approximately one in five incidents involves healthcare facilities).
The situation in Italy is particularly concerning: the number of cyber attacks against healthcare entities increased by 83% in the first half of 2024 compared to the same period the previous year, according to the Clusit 2024 Report. This is a dramatic increase, a sign of a dangerous escalation that began in recent years and has been accelerated by the post-pandemic context and the growing digitalization of healthcare (Report by the National Cybersecurity Agency 'The Cyber Threat to the Healthcare Sector').
This alarming trend has specific roots. Hackers see healthcare facilities as a "rich" target from several perspectives. First, health data is extremely sensitive and valuable: stealing medical records, lab reports, and patients' personal information allows criminals to demand high ransoms, sell data on the dark web, or use it for identity fraud. Additionally, hospitals and medical centers provide critical, uninterruptible services: an attack that locks down IT systems can literally endanger people's lives.
This urgency often pushes victims to quickly pay a ransom in order to restore operations, making the sector a lucrative target. Unfortunately, many healthcare organizations also suffer from outdated or insecure IT systems, with cybersecurity budgets traditionally limited compared to other sectors — a factor that makes them vulnerable to intrusions if they don't take action.
High-Profile Cyber Attack Cases in Healthcare
August 2021: One of the first major cases was the ransomware attack that hit the IT systems of the Lazio Region during the anti-Covid vaccination campaign. On that occasion, criminals managed to block the regional vaccine booking portal for several days, using malware introduced through the credentials of an external supplier, causing enormous disruption to the population and the vaccination campaign.
February 2023: Hospital Service S.p.A., an Italian company providing outsourcing and logistics services to many hospitals, suffered a supply-chain attack by the ransomware group RansomHouse, which managed to steal approximately 50 GB of data, potentially putting the client healthcare facilities at risk.
May 2023: The IT system of ASL 1 Abruzzo was locked down by a ransomware attack carried out by the criminal group Monti, who infected and encrypted the entire ASL IT system, paralyzing all provincial healthcare services. Doctors and staff had to resort to pen and paper for weeks, with appointments and tests managed manually and enormous disruption to patients. The hackers stole 363 GB of health data and, after the organization refused to pay the ransom, published it online. It was one of the worst recent healthcare breaches, with severe operational, legal, and reputational consequences.
June 2023: A cyber attack hit the Centro Diagnostico Basile in Naples, part of the Cerba HealthCare group. After reports of online service disruptions, the company discovered that a server had been compromised through a phishing email containing malware. The criminals attempted to extort a payment by threatening to release the stolen data, but Cerba HealthCare refused to give in to the blackmail and immediately took the website and online services offline, activating alternative procedures (call center and service desks) to still ensure bookings.
October 2023: A ransomware breach hit the AOUI of Verona, where regular services were interrupted and 612 GB of data was compromised. The attack was claimed by the Rhysida group, which demanded a ransom of 10 Bitcoin, equivalent to over €300,000, and published part of the data on the dark web. The episode highlighted the fragility of large Italian hospital facilities in the face of these threats occurring on an almost monthly basis, as evidenced by several reports.
April 2024: The Russian group Black Basta attacked Synlab Italia, paralyzing over 380 laboratories. The company was forced to suspend all diagnostic activities for days. The hackers stole an enormous amount of confidential information — approximately 1.5 terabytes of sensitive patient data, including test results and personal data — demanding a multimillion-euro ransom that Synlab refused to pay, reporting the incident to authorities. In response, the cyber gang published the entire trove of stolen data on the dark web, causing nationwide repercussions, blocking millions of medical tests, and putting a vast number of patients' privacy at risk.
These examples clearly show the breadth of the cyber threat in healthcare. But how do these attacks actually happen? Let us now examine the most common attack vectors used against healthcare organizations.
The Most Common Attack Vectors
Hackers employ various techniques to breach healthcare IT defenses. In many cases they combine multiple methods, but 3 attack vectors stand out for their frequency and effectiveness against hospitals and healthcare organizations:
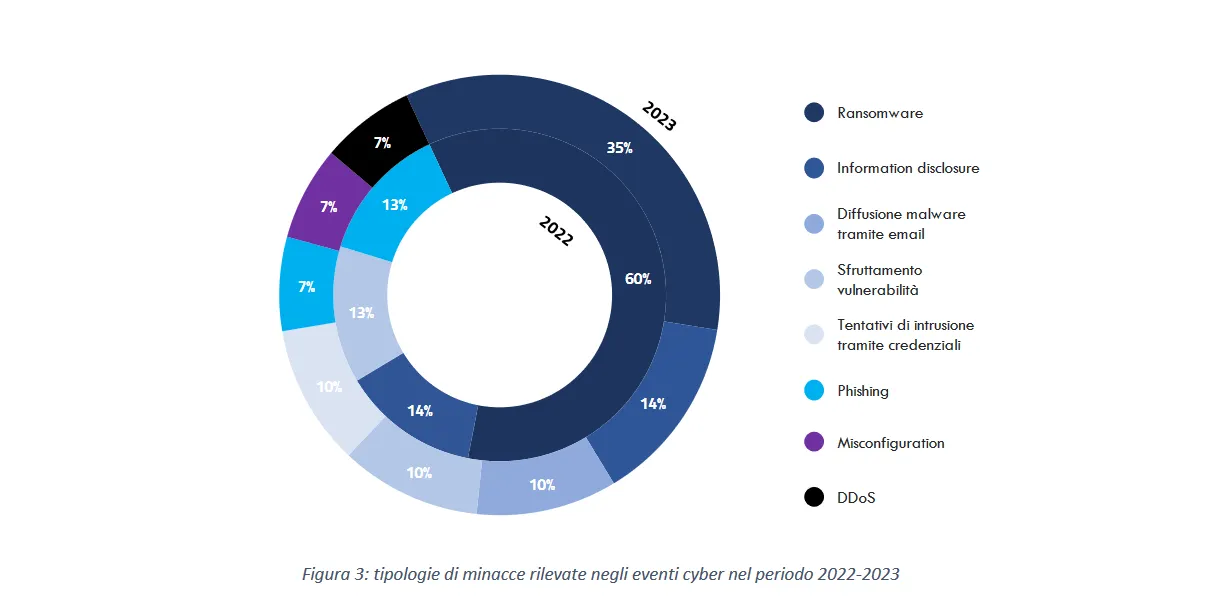
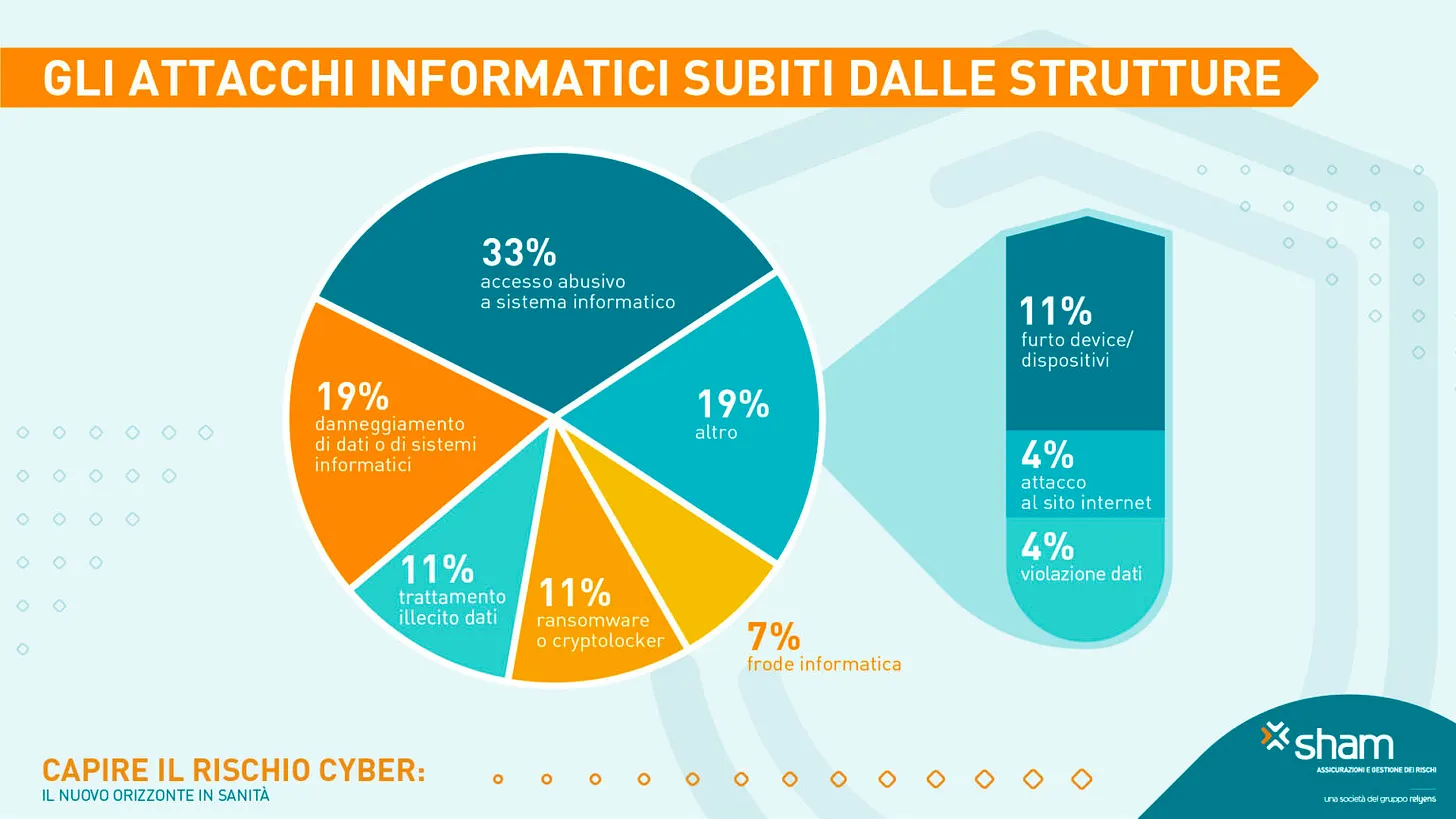
Ransomware: This is the most dangerous threat, encompassing both "malware" — a computer virus used to encrypt data and servers, making IT systems inaccessible, and "ransom" — i.e., an economic demand for payment. This is why it's called "double extortion": in addition to the operational lockdown, criminals steal data and threaten to release it. The consequences are severe: disruption of healthcare services and massive privacy violations. In 2023, over a third of cyber attacks in healthcare were caused by ransomware, according to the report by the National Cybersecurity Agency 'The Cyber Threat to the Healthcare Sector'.
Phishing and social engineering: Phishing is a cyber fraud technique in which hackers send seemingly legitimate communications (e.g., emails that appear to come from health authorities, known suppliers, or colleagues) to trick the victim into clicking a malicious link or opening an infected attachment. Beyond emails, scammers also use broader social engineering techniques: for example, posing as IT technicians on the phone to obtain passwords, or sending SMS messages (smishing) that lure victims into entering credentials on fake websites.
Supply chain attacks: Attacks that target external suppliers or technology partners of the healthcare facility in order to then spread to the facility itself and all its client organizations.
How to Strengthen Cybersecurity in Healthcare: 4 Practical Solutions
The growing attention to this issue has led the National Cybersecurity Agency (ACN) to launch several strategic initiatives, such as preventive actions through continuous monitoring, rapid response post-attack to immediately restore essential services, and extensive training. But it's not just about operational best practices — the European legislator has also recognized healthcare as critical infrastructure by introducing the NIS 2 Directive (Network and Information Security). The NIS 2, which came into force in January 2023, is a directive that extends security obligations to hospitals, laboratories, and healthcare technology suppliers, requiring the adoption of rigorous prevention and incident response measures (e.g., periodic audits, reporting within 24 hours, and penalties for non-compliance).
This means that cybersecurity is no longer just a technical option, but a regulatory obligation. The protection of data, infrastructure, and operational continuity is now an integral part of compliance, on par with privacy or clinical safety.
In addition to institutional interventions, every healthcare organization must also act on 4 key fronts, including:
1. Staff Training and Phishing Training
Human error is the first vulnerability to address. It is essential to train all staff — medical, administrative, and technical — on good digital practices, such as:
recognizing suspicious emails
using strong passwords
avoiding unverified websites
immediately reporting any phishing attempts
Innovative tools like ImmuniScam, powered by Artificial Intelligence, enable the simulation of realistic attacks and strengthen staff readiness.
2. Protection Technologies and Continuous Monitoring
Training alone is not enough: solid technological barriers are also needed. Every facility should equip itself with advanced technologies capable of blocking threats before they cause damage:
next-generation antivirus/EDR solutions,
firewalls and IDS/IPS systems to monitor the network,
SIEM solutions and SOC services active 24/7 to detect and manage anomalies in real time.
3. Secure Backups and Business Continuity Plans
Eliminating risk entirely is impossible, but limiting its impact is essential:
perform frequent backups of critical data, stored offline or in isolated cloud environments,
have a business continuity plan to keep services running even during an IT emergency (e.g., paper forms, alternative protocols),
conduct periodic disaster recovery drills to test the organization's response.
4. Constant Updates and Vulnerability Management
Many cyber attacks succeed because they exploit known but never-patched technical flaws. It is therefore necessary to:
implement a rigorous patch management program,
regularly update all software and devices,
adopt advanced access controls (e.g., MFA and least privilege),
carefully assess IT suppliers' security through audits and stringent contracts.
Conclusion
The digitalization of Italian healthcare has improved efficiency but has also increased exposure to cyber threats. Regulations such as the European DORA (the European regulation on digital operational resilience) and national guidelines (GDPR, AgID/ACN requirements for public administration, etc.) impose greater controls on suppliers and promote compliance as a lever for security.
In this context, preventive maintenance and access management become essential for limiting risks. The growth of cyber attacks makes it urgent to integrate cybersecurity into the daily management of healthcare facilities, just as is done for Privacy or clinical Hygiene.
The solutions exist, but what is needed is widespread awareness: protecting data and ensuring continuity of care is a strategic responsibility, not an accessory cost. Only then can our healthcare system withstand hacker attacks and continue to protect what matters most: the health and data of citizens.
Related Articles
6 Common Horror Stories in a Healthcare Reception
Explore the most critical and common situations that occur at healthcare receptions and discover how to prevent them through innovative solutions.
Read moreThe Voice Revolution: Voicebot Alternatives to GAIA
Discover how voicebots are transforming Italian healthcare, offering efficient and accessible solutions for call management and patient interaction.
Read more